Last year will be characterized by hacking and interference in the American political system. It was a huge wake up call for everybody involved in politics; InfoSec was an important priority.
I don't live in America. I live in the tiny Australian Capital Territory, a territory comprising of a Canberra; a city of 300,000 people. Like many places, we have a local government full of politicians. I analyzed the websites of the 25 MLAs (members of the legislative assembly) and their parties sites.

Spolier: too many local politicians have SQL injection vulnerable sites, and don't even care.
Methodology
I'm not an InfoSec industry professional; just a developer who is interested in this stuff. This is not a blog post about novel vulnerabilities - is is a story about bad higyine.
First, I compiled a list of all the sites. In total, there are 17 MLA sites (not all MLAs have their own site) and 3 party sites. There is even a helpful list maintained by the government.
Then I used used the http headers to do l33t hax0r discovery of the server software they used. It was as follows:
| Software Package | # of Users |
|---|---|
| Wordpress | 7 |
| NationBuilder (SaaS) | 4 |
| Wix (SaaS) | 2 |
| Unknown/Bespoke | 2 |
| Static | 1 |
| Wordpress.COM | 1 |
The party sites used NationBuilder (ACT Labor), Wordpress (Canberra Liberals) and Dupral 7 (Greens). I found it very interesting here that software was divided between left wing and right wing parties. For example, NationBuilder was only used by left wing parties, despite pledging to be a non-partisan provider.
Inspecting the sites
So we have a mix of multiple types of sites. I'm no genius, so I assumed that Wix, Wordpress.com, the static site and NationBuilder (a rails based SaaS) were secure. They have companies behind them making sure that they are secure.
Fun fact: only 1 of the sites used HTTPS by default! Welcome toSo then I turned to the remaining 8 Wordpress sites (including the Canberra Liberals website). Wordpress has databases full of vunerabilities, especially when you count themes/plugins. A tool called wp-scan automates the plugin & version detection process and can print out a list of vulnerabilities that effect a given WP site. I used this to investigate the sites.
A whopping 5 out of the 8 sites were affected by serious vulnerabilities:
1. Andrew Wall
Andrew Wall MLA's site is a disaster. I'm not including a link because it is so inscure. He uses Wordpress, on a server with Microsoft IIS/7.0, that reports it is X-Powered-By: ASP.NET. It uses Wordpress 3.6, which was released in 2013! Wordpress 3.6 is ancient and full of vulnerabilities, including; unauthenticated stored XSS, unauthenticated post category modification and path traversal. The gallery plugin used also has an arbitrary file upload & CSRF issue.
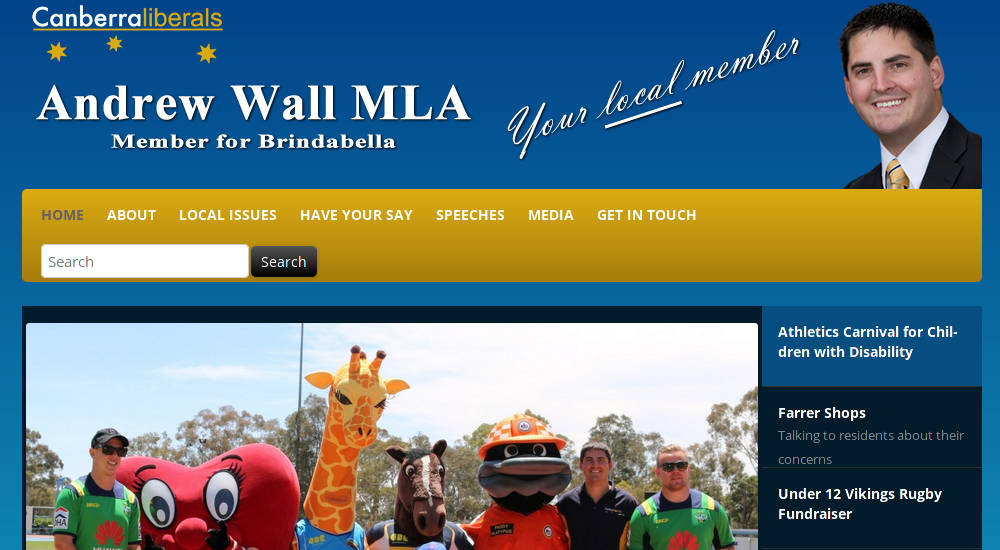
I contacted Andrew 3 times (12th, 16th and 31th of January), to no response. He should really consider getting a new website before it is defaced or hacked into an "online pharma" store.
2. Canberra Liberals
The Canberra Liberals have a donation button on their site. That would be great, except they use an outdated version of WooCommerce from 2014. It features many security issues; from object injection to persistent XSS.
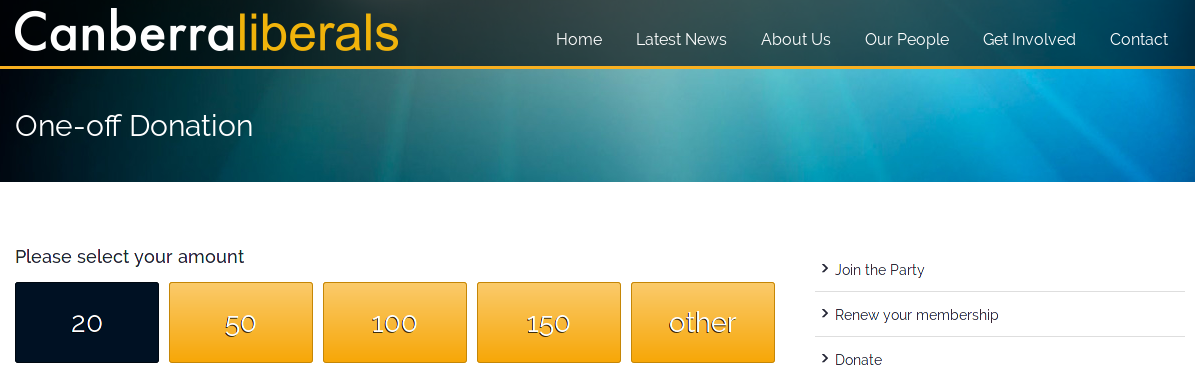
I don't know how hard it is to update a Wordpress plugin; but it is too hard for the Canberra Liberals. I contacted them 3 times (same as above) to no response. Nice to see security is valued!
3. Tara Cheyne
Wordpress again, with the Jetpack plugin. It is out of date and contains Stored XSS in addition to multiple other security issues.
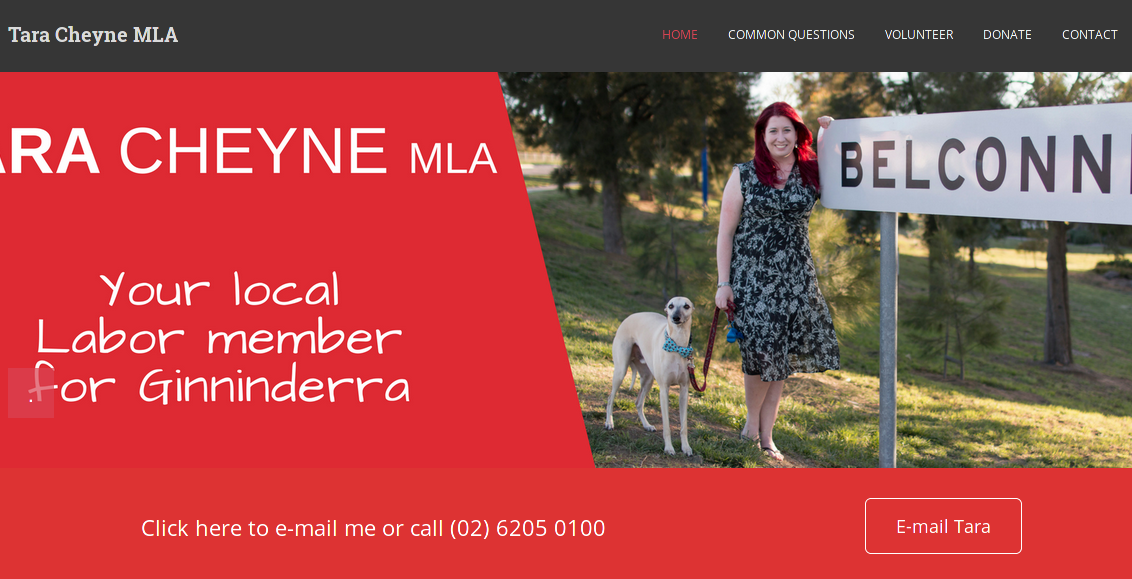
"E-mail Tara"; well I tried that!
I contacted Tara 3 times (same as above) to no response.
4. Mick Gentleman
Wordpress again. He uses a slightly outdated version of wordpress (4.6.1 from September 2016), which contains many vulnerabilities. They include a SQL injection issue and XSS.
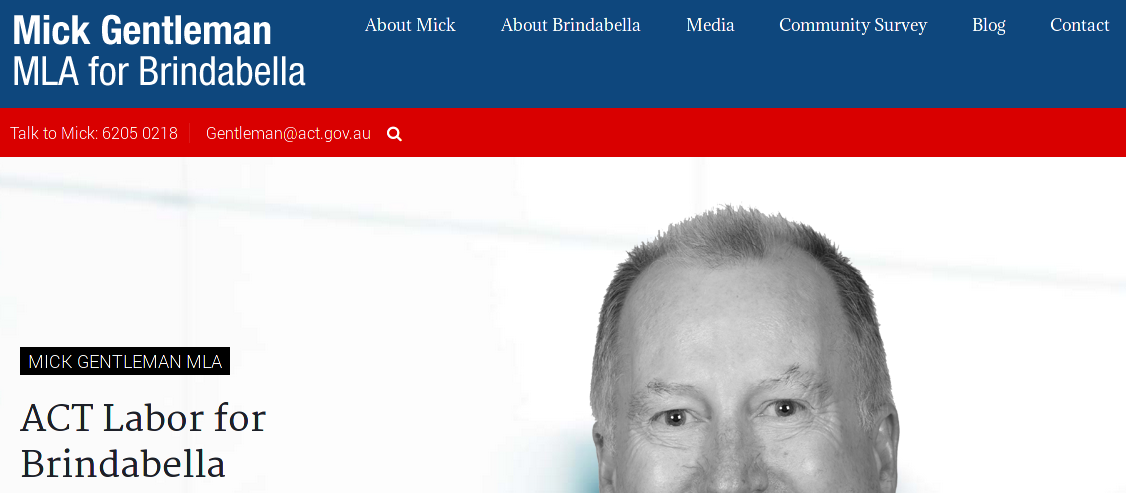
I contacted Mick 3 times (same as above) to no response. Starting to see a pattern here!
5. Mark Parton
Wordpress again, this time with an outdated Yoast SEO plugin. It contained 2 issues, Settings exposure and XSS again.
Mark was very co-operative. He responded to my 2nd email and informed me that he was not actively involved with the site any more.
Conclusions
When you include the party sites, 13 out of the 25 politicians had a outdated and vulnerable Wordpress sites. Most did not reposed to the information presented, even if it mean replying to an email reporting the issue. I'd really hate to see these sites be defaced or used to find private information on any of my local politicians.
While we focus on glamorous political hacking events such as during the US Presidential election, we need to realise the role of local government. Basic security hygiene isn't hard - they just need to stay up to date. Check up on your local members, so that they don't get defaced or hacked during their next elections!
I hope you enjoyed this article. Contact me if you have any thoughts or questions.
© 2015—2026 Sam Parkinson